- Microsoft Defender Atp Csp
- Microsoft Defender Atp Antivirus
- Microsoft Defender Atp E3
- Microsoft Defender Atp Dlp
- Microsoft Defender Atp Pricing
- Microsoft Defender ATP is an incredibly powerful post-breach solution that provides automated endpoint detection and response. Formerly known as Windows Defender ATP (or WDATP), Microsoft rebranded the product to reflect the fact that it is now also available on other operating systems (OSs) such as macOSX, Linux and Android.
- Microsoft Defender ATP is a unified endpoint security platform for preventative protection, post-breach detection, automated investigation, and response. Microsoft Defender ATP uses the following combination of technology built into Windows 10 and Microsoft’s robust cloud service: Aruba & Microsoft Defender Advanced Threat Protection.
- Microsoft Defender ATP. Microsoft Defender Advanced Threat Protection (ATP) is a threat detection and response product that is available on a free trial or subscription basis. You can configure Microsoft Defender ATP as a Third Party Alert event source in InsightIDR, which allows you to parse onboarded system logs through an API.
- Microsoft Defender Plan 2 cover Office 365 Plan 1 capabilities (Safe Attachments, Safe Links, ATP for SharePoint, OneDrive, and Microsoft Teams, Anti-phishing in Defender for Office 365 protection, Real-time detections) plus Automation, investigation, remediation, and education capabilities ( Threat Tracker, Threat Explorer, Automated.
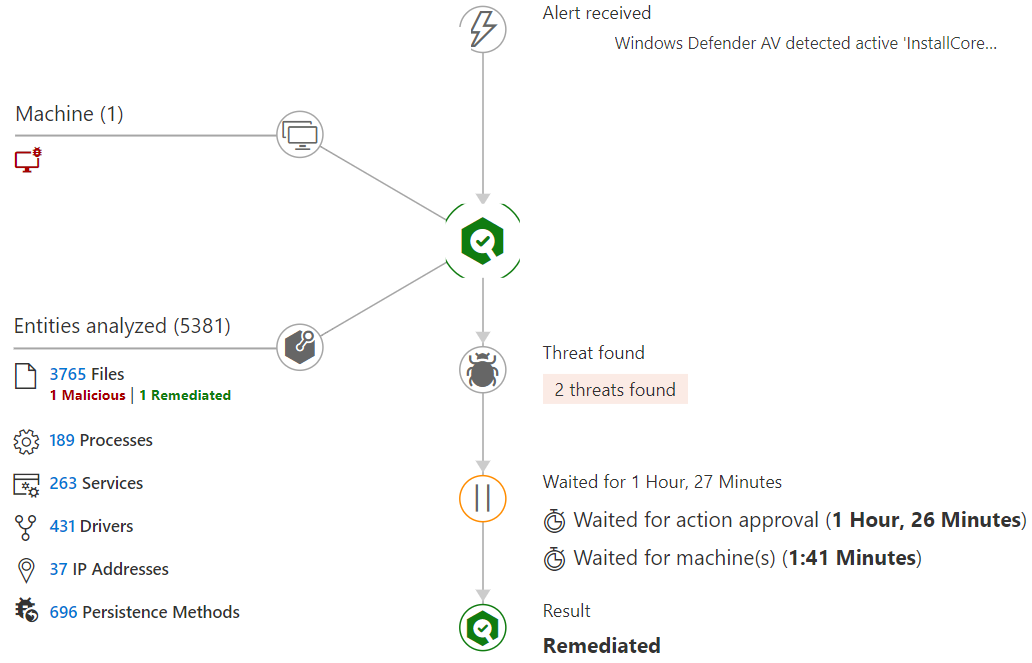
Windows Defender ATP can now leverage automated memory forensics to incriminate memory regions and perform required in-memory remediation actions. With this new unique capability, we are shifting from simply alerting to a fully automated investigation and resolution flow for memory-based attacks. This increases the range of threats addressable.
Applies to:
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
This topic describes how to install, configure, update, and use Defender for Endpoint on Android.
Caution
Running other third-party endpoint protection products alongside Defender for Endpoint on Android is likely to cause performance problems and unpredictable system errors.

Microsoft Defender Atp Csp
How to install Microsoft Defender for Endpoint on Android
Prerequisites
For end users
Microsoft Defender for Endpoint license assigned to the end user(s) of the app. See Microsoft Defender for Endpoint licensing requirements
Intune Company Portal app can be downloaded from GooglePlayand is available on the Android device.
- Additionally, device(s) can beenrolledvia the Intune Company Portal app to enforce Intune device compliancepolicies. This requires the end user to be assigned a Microsoft Intune license.
For more information on how to assign licenses, see Assign licenses tousers.
For Administrators
Access to the Microsoft 365 Defender portal.
Note
Microsoft Intune is the only supported Mobile Device Management (MDM) solution for deploying Microsoft Defender for Endpoint on Android. Currently only enrolled devices are supported for enforcing Defender for Endpoint on Android related device compliance policies in Intune.
Access Microsoft Endpoint Manager admincenter, to deploy theapp to enrolled user groups in your organization.
Network Requirements
- For Microsoft Defender for Endpoint on Android to function when connected to a network the firewall/proxy will need to be configured to enable access to Microsoft Defender for Endpoint service URLs.
System Requirements
Mobile phones running Android 6.0 and above. Tablets and other mobile devices running Android are not currently supported.
Intune Company Portal app is downloaded from GooglePlayand installed. Device enrollment is required for Intune device compliance policies to be enforced.
Installation instructions
Microsoft Defender for Endpoint on Android supports installation on both modes ofenrolled devices - the legacy Device Administrator and Android Enterprise modes.Currently, Personally-owned devices with work profile and Corporate-owned fully managed user device enrollments are supported in Android Enterprise. Support for other Android Enterprise modes will be announced when ready.
Deployment of Microsoft Defender for Endpoint on Android is via Microsoft Intune (MDM).For more information, see Deploy Microsoft Defender for Endpoint on Android with Microsoft Intune.
Note
Microsoft Defender for Endpoint on Android is available on Google Play now.
You can connect to Google Play from Intune to deploy Microsoft Defender for Endpoint app, across Device Administrator and Android Enterprise entrollment modes.
How to Configure Microsoft Defender for Endpoint on Android
Guidance on how to configure Microsoft Defender for Endpoint on Android features is available in Configure Microsoft Defender for Endpoint on Android features.
Related topics
-->Applies to:
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Microsoft Defender Atp Antivirus
For more info about Windows 10 Enterprise Edition features and functionality, see Windows 10 Enterprise edition.
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats.
Defender for Endpoint uses the following combination of technology built into Windows 10 and Microsoft's robust cloud service:
Endpoint behavioral sensors: Embedded in Windows 10, these sensors collect and process behavioral signals from the operating system and send this sensor data to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
Cloud security analytics: Leveraging big-data, device-learning, andunique Microsoft optics across the Windows ecosystem,enterprise cloud products (such as Office 365), and online assets, behavioral signalsare translated into insights, detections, and recommended responsesto advanced threats.
Threat intelligence: Generated by Microsoft hunters, security teams,and augmented by threat intelligence provided by partners, threatintelligence enables Defender for Endpoint to identify attackertools, techniques, and procedures, and generate alerts when theyare observed in collected sensor data.
Microsoft Defender for Endpoint
Threat & Vulnerability Management | Attack surface reduction | Next-generation protection | Endpoint detection and response | Automated investigation and remediation | Microsoft Threat Experts | |
Tip
- Learn about the latest enhancements in Defender for Endpoint: What's new in Microsoft Defender for Endpoint.
- Microsoft Defender for Endpoint demonstrated industry-leading optics and detection capabilities in the recent MITRE evaluation. Read: Insights from the MITRE ATT&CK-based evaluation.
Threat & Vulnerability Management
This built-in capability uses a game-changing risk-based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations.
Attack surface reduction
The attack surface reduction set of capabilities provides the first line of defense in the stack. By ensuring configuration settings are properly set and exploit mitigation techniques are applied, the capabilities resist attacks and exploitation. This set of capabilities also includes network protection and web protection, which regulate access to malicious IP addresses, domains, and URLs.
Next-generation protection
To further reinforce the security perimeter of your network, Microsoft Defender for Endpoint uses next-generation protection designed to catch all types of emerging threats.
Endpoint detection and response
Endpoint detection and response capabilities are put in place to detect, investigate, and respond to advanced threats that may have made it past the first two security pillars. Advanced hunting provides a query-based threat-hunting tool that lets you proactively find breaches and create custom detections.
Automated investigation and remediation
In conjunction with being able to quickly respond to advanced attacks, Microsoft Defender for Endpoint offers automatic investigation and remediation capabilities that help reduce the volume of alerts in minutes at scale.
Microsoft Secure Score for Devices
Defender for Endpoint includes Microsoft Secure Score for Devices to help you dynamically assess the security state of your enterprise network, identify unprotected systems, and take recommended actions to improve the overall security of your organization.
Microsoft Defender Atp E3

Microsoft Threat Experts
Microsoft Defender for Endpoint's new managed threat hunting service provides proactive hunting, prioritization, and additional context and insights that further empower Security operation centers (SOCs) to identify and respond to threats quickly and accurately.
Important
Defender for Endpoint customers need to apply for the Microsoft Threat Experts managed threat hunting service to get proactive Targeted Attack Notifications and to collaborate with experts on demand. Experts on Demand is an add-on service. Targeted Attack Notifications are always included after you have been accepted into Microsoft Threat Experts managed threat hunting service.
If you are not enrolled yet and would like to experience its benefits, go to Settings >General >Advanced features >Microsoft Threat Experts to apply. Once accepted, you will get the benefits of Targeted Attack Notifications, and start a 90-day trial of Experts on Demand. Contact your Microsoft representative to get a full Experts on Demand subscription.
Centralized configuration and administration, APIs
Integrate Microsoft Defender for Endpoint into your existing workflows.
Microsoft Defender Atp Dlp

Integration with Microsoft solutions
Defender for Endpoint directly integrates with various Microsoft solutions, including:
- Azure Defender
- Azure Sentinel
- Intune
- Microsoft Cloud App Security
- Microsoft Defender for Identity
- Microsoft Defender for Office
- Skype for Business
Microsoft Defender Atp Pricing
Microsoft 365 Defender
With Microsoft 365 Defender, Defender for Endpoint and various Microsoft security solutions form a unified pre- and post-breach enterprise defense suite that natively integrates across endpoint, identity, email, and applications to detect, prevent, investigate, and automatically respond to sophisticated attacks.